Introducing CAPTOR Compliance
Josh Bohls
Reporting & Alert System for Data Leakage Protection (DLP) Violations and Insider Threats
Enterprise Mobility Management (EMM) platforms go a long way to protecting corporate data, managing devices and apps, and enabling secure mobile use cases - but there are gaps. DLP and container policies can block certain actions, but they do not cover all potential data leakage opportunities or insider threats. They have also fallen short in logging and reporting when employees attempt to violate data protection policies. Here are some examples where EMM policies and controls do not do enough to protect corporate data:
Taking a screenshot of a protected document or photo on an unsupervised iOS device
Screen mirroring to an TV or monitor
Screen recording on an unsupervised device
Attempts to share/copy content and files to unauthorized apps or cloud services
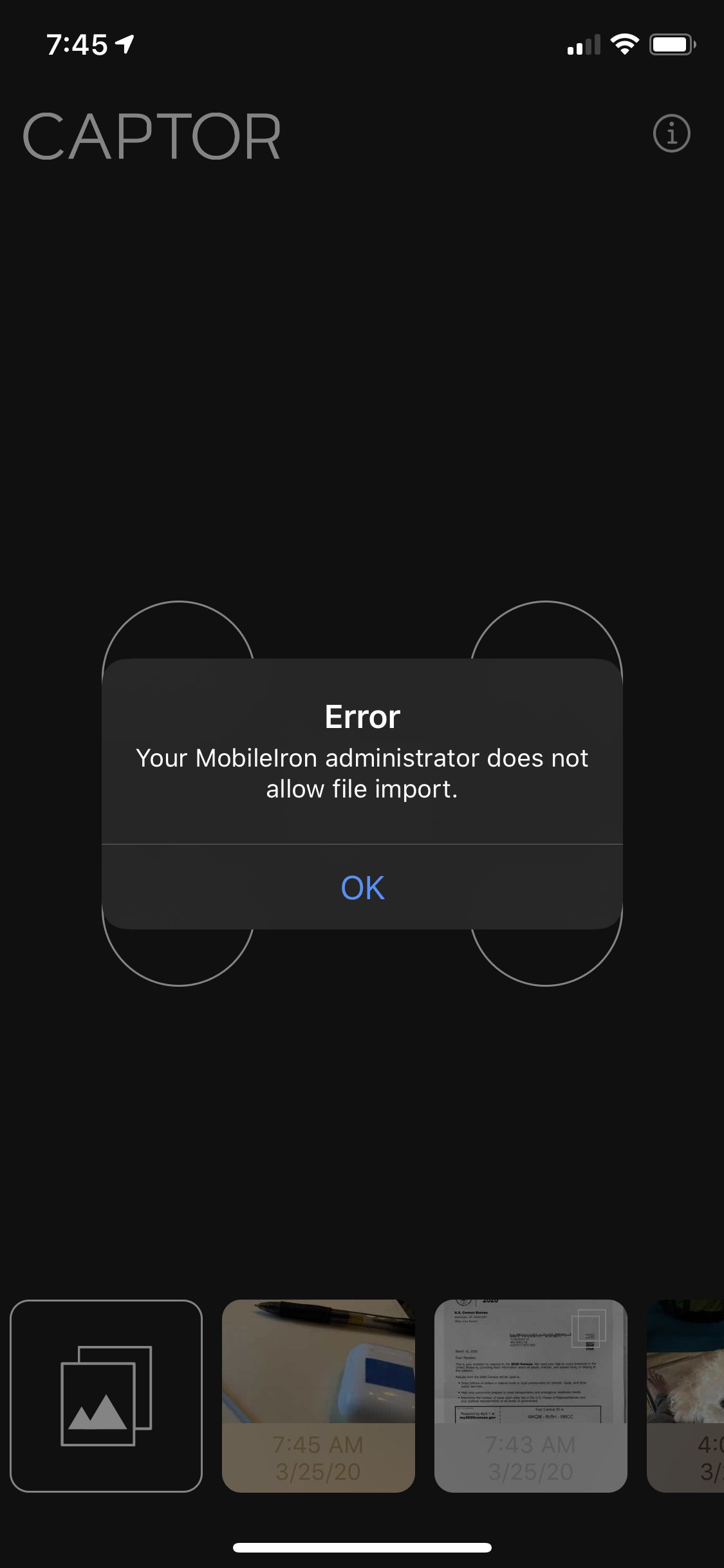
Attempts to import/copy content and files into the secure container from an unauthorized app or cloud service.
Attempts to use bluetooth services such as AirDrop® to share files to an unauthorized mobile device
CAPTOR Compliance Fills a Critical IT Knowledge Gap
CAPTOR Compliance is a new component of Inkscreen’s secure content capture app ecosystem for logging and alerting IT Administrators when employees violate -or attempt to violate- corporate DLP or container policies. This information is critical and actionable. No longer will IT be in the dark when employees exploit workarounds to established EMM policies.
When enabled, CAPTOR Compliance silently logs possible violations as employees use the CAPTOR mobile app. Events can be logged even if the user is operating the app in a disconnected state without access to wifi or cellular signals. These events are then collected in a secure database and reported to the company’s EMM admin on a scheduled basis - immediately, daily, weekly, or monthly.
CAPTOR Compliance Report Example
The report identifies the employee, time/date of the event, location of the event, type of device used, and event type.
CAPTOR Compliance will initially focus on the following events, with more to be added over time:
Screenshots - Employee views a photo or document and creates a screenshot, which is saved outside of the container.
Unauthorized Share - Employee attempts to use the Open In options to copy content to an app or service that is blocked.
Unauthorized Import - Employee attempts to use the Open In option to copy content into CAPTOR from a blocked app.
Screen Recording - Employee initiates a screen recording session that includes CAPTOR.
Screen Mirroring - Employee opens CAPTOR while mirroring their screen on a monitor or TV
CAPTOR Compliance is available as part of a free trial and an optional upgrade to the CAPTOR secure content capture mobile app.